: Automatic Verification of Internet Data-paths
: Automatic Verification of Internet Data-paths
What we do
Challenges we overcome
The core problem when operating through unknown or non-cooperative commercial 5G infrastructure is that the unknown infrastructure potentially exposes communications to an adversary.

Risks of non-cooperative infrastructure
When communications traverse adversary-controlled infrastructure, it allows DOD’s sophisticated adversaries to recognize, disrupt, or extract intelligence from the communications. Even encrypted communications reveal the communicating source and destination IP addresses, which leaves the traffic remain vulnerable to advanced analysis techniques able to extract information directly from the encrypted data portion.

Obfuscation Techniques offer Limited Protection
Disguising traffic in hopes of evading adversary detection may work at first, but such disguises create an arms race with ever more sophisticated disguises and advanced network intelligence techniques to detect them. With each new obfuscation attempt, DOD will never know if the disguise fools the adversary or if the adversary is simply lulling them into a false sense of security. Worse still, once an adversary learns DOD’s obfuscation approaches, the disguises themselves can unintentionally draw unwanted attention from that adversary.
Fundamentally, traffic obfuscation cannot provide meaningful security guarantees when the underlying infrastructure is an unknowable black box.
Our solution:
We propose the AVOID system - Automated Verification Of Internet Data-paths – that creates an unprecedented capability through two deliverables that tackle two high risk attack vectors for 5G communications.
Approach 1
Avoid initiating communications with adversarial base stations
Several governments have reported that Chinese intelligence can control Huawei and ZTE base stations anywhere in the world, which would allow them to observe all traffic passing through those base stations.
AVOID leverages deep learning to recognize potentially malicious 5G base station vendors in seconds. AVOID also provides a mechanism for DOD devices to connect to specific benign base stations.
Approach 2
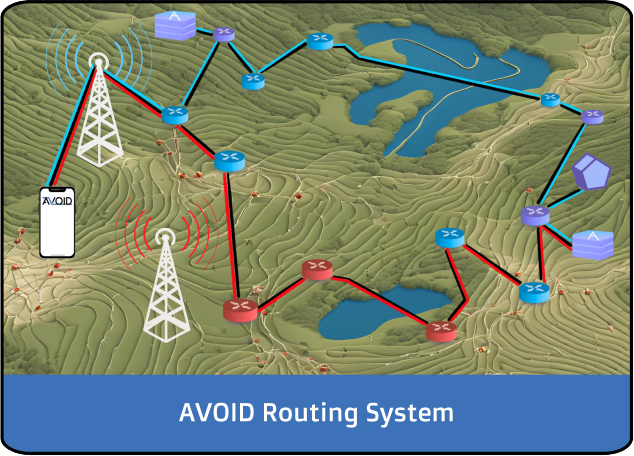
AVOID untrusted communications infrastructure along entire path
AVOID embeds topologic and geographic awareness into an overlay routing system, providing a mechanism for DOD’s communications to avoid adversary-controlled territory across the global Internet and route communication along benign paths.
Solving DOD’s biggest communication challenges
The outcome will be an end-to-end adversary avoidance routing system that does not require modification to existing applications or routers in DOD networks, nor cooperation by any third-party network.
-
Embed topologic and geographic awareness into the routing system
-
Ensure DOD communications avoid adversary-controlled infrastructure
-
Provide safe communication network paths to DOD-controlled networks
Competitive Advantages

Leverages Existing Commercial 4G/5G infrastructure
- Instant & ubiquitous communications
- Cheap commercial equipment (phones and hotspots)
- WiFi-to-5G hotspot capability that can compute and modify data and control layers
- No cost to maintain or deploy infrastructure

Allows Soldiers To Use Personal Phones
No other solution addresses this problem
- Other solutions puts service members (and DOD) at risk
- AVOID deals with operational reality
Partners
The AVOID project is led by PI Alexander Marder at Johns Hopkins University, and involves a number of member institutions:







Funding Support
The Automated Verification Of Internet Data-paths for 5G project is funded by the U.S. Office of the Under Secretary of Defense for Research and Engineering (OUSD(R&E)), and the U.S. National Science Foundation (NSF) via Convergence Accelerator grants ITE-2226460 5G Traffic Sovereignty: Operating Through an Adversarial Internet and ITE-2326928 Automated Verification Of Internet Data-paths for 5G. The views and conclusions contained herein are those of the authors and should not be interpreted as necessarily representing the official policies or endorsements, either expressed or implied, of the OUSD(R&E) and NSF.